When businesses are looking to move all or part of their operations to the cloud, there is the inevitable question of “security”. Will our website be safe in the cloud? Does hosting our application data in the cloud make our business more vulnerable to cyber attacks? Can our cloud servers handle a DDoS attack? What is cloud security and what is the right way to implement it for our business?
What is Cloud Security?
 Security in the cloud is much like security in your on-premises data centers – only without the costs of maintaining facilities and hardware. In the cloud, you don’t have to manage physical servers or storage devices. Instead, you use software-based security tools to monitor and protect the flow of information into and of out of your cloud resources.
Security in the cloud is much like security in your on-premises data centers – only without the costs of maintaining facilities and hardware. In the cloud, you don’t have to manage physical servers or storage devices. Instead, you use software-based security tools to monitor and protect the flow of information into and of out of your cloud resources.
Cloud security provides multiple levels of controls within the network infrastructure in order to provide continuity and protection for cloud-based assets like websites, web applications and data. Whether in a public or private cloud, businesses need to balance DDoS protection, high availability, data security, and regulatory compliance in their cloud security provider.
Cloud Security Challenges
- DDoS attacks
- Data breaches
- Insufficient Identity, Credential, and Access Management
- Data loss
- Insecure access points (APIs)
- System Vulnerabilities
- Cloud Account Hijacking
- Malicious Insiders
- Shared Technology Vulnerabilities
- Notifications and alerts
Whose is responsible for Cloud Security?
 When you move computer systems and data to the cloud, security responsibilities become shared between consumer and cloud service provider. In this case, the cloud provider is responsible for securing the underlying infrastructure that supports the cloud and the customer is responsible for responsible for anything you put on the cloud or connect to the cloud. This shared security responsibility model can reduce consumer operational burden in many ways, and in some cases may even improve consumer default security posture without additional action on consumer part.
When you move computer systems and data to the cloud, security responsibilities become shared between consumer and cloud service provider. In this case, the cloud provider is responsible for securing the underlying infrastructure that supports the cloud and the customer is responsible for responsible for anything you put on the cloud or connect to the cloud. This shared security responsibility model can reduce consumer operational burden in many ways, and in some cases may even improve consumer default security posture without additional action on consumer part.
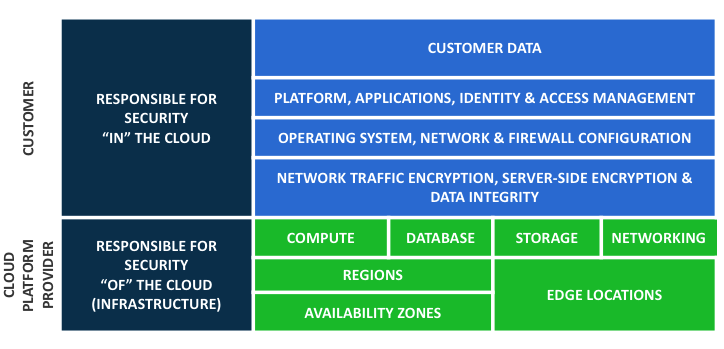
The best practice is for enterprises to carefully review the cloud service provider’s service level agreement (SLA) to understand the enterprise’s responsibility of enforcing security measures for all cloud service models.
Levels of Cloud Security
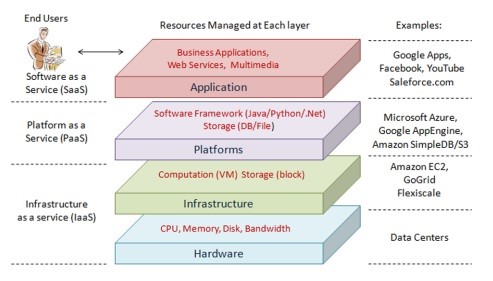 The cloud security is to focus on the various levels of infrastructure that require protection.
The cloud security is to focus on the various levels of infrastructure that require protection.
- Software-as-a-service (SaaS)
- Infrastructure-as-a-service (IaaS)
- Platform-as-a-service model (PaaS)
If you look at a multi-level infrastructure model, all the way at the bottom of the model is the IaaS, followed by the PaaS and then SaaS. These are the three levels of cloud security every business needs to protect.
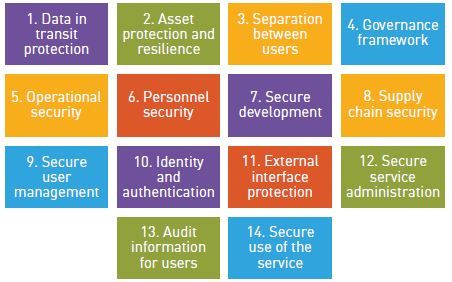
Cloud Security Design Principles
-
Governance framework
When procuring a cloud service, ensure that the supplier has a suitable security governance framework in place. A governance framework will ensure that procedure, personnel, physical and technical controls remain effective through the lifetime of the service, in response to changes in the service, and changes in threat and technology development.
-
Operational security
The service provider should have processes and procedures in place to ensure the operational security of the service. The service will need to be operated and managed securely in order to detect or protect attacks against it.
-
Data in transit protection
Consumer data transiting network should be adequately protected against integrity and confidentiality. This should be achieved via network protection and encryption.
-
Asset protection and resilience
Consumer data, and the assets storing or processing it, should be protected against physical tampering, loss, damage or seizure.
-
Separation between consumers
Separation between different consumers of the service prevents one malicious or compromised consumer from affecting the service or data of another. The service model (IaaS, PaaS, and SaaS), the deployment model (private, public, etc.) and the level of assurance available in the implementation of separation controls are affects the implementation of separation consumers.
-
Identity and authentication
Consumer and service provider access to all service interface should be constrained to authenticated and authorized individuals.
All cloud services will have some requirement to identify and authenticate users wishing to access service interfaces. Weak authentication or across control may allow unauthorized changes to a consumer’s service, theft or modification of data, or denial of service.
It is also important that authentication occurs over secure channels. Use of insecure channels such as email, HTTP or telephone can be more vulnerable to interception or social engineering attacks. -
External interface protection
All external or less trusted interfaces of the service should be identified and have appropriate protections to defend against attacks through them.
If an interface is exposed to consumers or outsiders and it is not sufficient robust, then it could be subverted by attackers in order to gain access to the service or data within it. If the interfaces exposed include private interfaces (such as management interfaces) then the impact may be more significant.
Consumers can use different models to connect to cloud services which expose their enterprise systems to varying levels of risk. -
Secure service administration
The methods used by the service provider’s administrators to manage the operational service should be designed to mitigate any risk of exploitation that could undermine the security of the service.
-
Personal security
Personnel within a cloud service provider with access to consumer data and systems need to be trustworthy. Service providers need to make clear how they screen and manage personnel within any privileged roles. Personnel in those roles should understand their responsibilities and receive regular security training.
-
Secure development
Services should be designed and developed to identify and mitigate threats to their security. Services which are not designed securely may be vulnerable to security issues which could compromise consumer data, cause loss of service or enable other malicious activity.
-
Supply chain security
The service provider should ensure that its supply chain satisfactorily supports all of the security principles that the service claims to implement.
Cloud services often rely upon third party products and services. Those third parties can have an impact on the overall security of the services. If this principal is not implemented then it is possible that supply chain compromise can undermine the security of the service and affect the implementation of other security principles. -
Secure consumer management
Consumers should be provided with the tools required to help them securely manage their service. Management interfaces and procedures are a vital security barrier in preventing unauthorized people accessing and altering consumer’s resources, applications and data.
-
Audit information provision to consumers
Consumer should be provided with the audit records they need to monitor access to their service and the data held within it.
The type of audit information available to consumers will have a direct impact on their ability to detect and respond to inappropriate or malicious usage of their service or data within reasonable timescales. -
Secure use of the service by the consumer
Consumers have certain responsivities when using a cloud service in order for their use of it to remain secure, and for their data to be adequately protected.
Major Cloud Providers and Security Services
- AWS Security Services – https://aws.amazon.com/products/security/
- GCP Security Services – https://cloud.google.com/security/products/?refresh=1
- Azure Security Services – https://docs.microsoft.com/en-us/azure/security/azure-security-services-technologies
- IBM Cloud Security Services – https://www.ibm.com/in-en/security/services/cloud-security-services
References
https://www.cdnetworks.com/cloud-security/what-is-cloud-security-and-what-are-the-benefits/
https://aws.amazon.com/security/introduction-to-cloud-security/
https://www.mercurysolutions.co/blog/7-top-cloud-security-challenges-and-solutions
https://cloudcheckr.com/2018/07/shared-responsibility-model/
https://www.whoa.com/fighting-the-top-12-threats-to-cloud-cyber-security-threats-10-12/
https://www.ncsc.gov.uk/collection/cloud-security?curPage=/collection/cloud-security/implementing-the-cloud-security-principles
Leave a Reply